Why Your IT Staff Cannot Secure Your Business
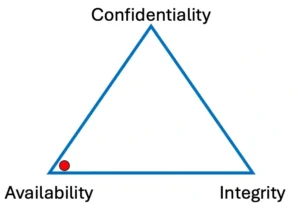
Big shout out to the people that keep our information systems running! Information Technology Staff fill a critical role in any business to ensure their technology solutions support business objectives and maintain reliable availability of systems and information throughout the enterprise. “Availability” is the key word for IT support. Availability, however, is just one of three critical aspects of information security. The concept of confidentiality, integrity, and availability is shown in the security model known as the CIA Triad.
Availability relates to functionality, up-time, and generally less control (e.g. everyone can use it, everyone can see it). Confidentiality relates to restricting assets to authorized users (e.g. a password controlled account login or encrypted storage and backups). Integrity relates to accountability of actions (e.g. a signed email or document, tracking who accesses an asset). When availability is the priority, confidentiality and integrity suffer. In this diagram, you can see the far distance from confidentiality and integrity, the two security points of the model. The more available the asset, the less confidentiality, the less integrity. In a healthy cybersecurity environment, the dot would be more toward the center. Businesses that store customer or patient information, intellectual property, trade secrets, or financial data should show an off-centered dot that’s closer to confidentiality.
If availability was the number one priority of your business, where would pricing power and quality fall?
Imagine a widget manufacturer who’s main driver is product availability. She knows that tens of thousands of people in her market need her widgets and she intends to serve them all. High availability requires that she won’t let anyone go without their widget because they can’t afford it. Manufacturing at that pace involves equipment maintenance expenses, perhaps spare equipment to ensure maximum uptime. It impacts her ability to maintain quality and could jeopardize the safety of her employees. Many other costs are associated with this approach but her focus on availability makes the business unsustainable.
A restaurant owner similarly prioritizing availability ensures every customer is fed. His focus on availability de-prioritizes profits and quality. Knowing this, everyone comes to his restaurant. The results? Long lines of customers waiting for a table or take out, overworked servers and kitchen staff, food and service quality degradation, and higher risks to employee safety. Prioritizing availability also kills his pricing power. He would soon realize that he can’t make a living without balancing availability with the other important business factors.
This diagram translates the CIA Triad to non technical business priorities.
While most Information Technology staff are aware that cybersecurity is important, they don’t have the skills and experience to implement it. They’re left with canned solutions found on the Internet that are costly and poorly configured that are ultimately ineffective and a waste of resources. They don’t often have the tools or skills to configure a vulnerability scan that reveals weaknesses that can be exploited by cyberattackers. They don’t know how to securely configure Data Loss Prevention, firewalls, or software access. They can keep your systems running, but they can’t analyze and reduce your threat surface (the ways attackers exploit your weaknesses). People buy and setup home Wi-Fi routers and just keep the default password from the manufacturer all the time. Sadly, that’s how IT staff manage cybersecurity.
Companies find out quickly just how ineffective their IT staff’s security efforts have been when they make their first cybersecurity hire. Having been that guy in several organizations, I can tell you how wasteful and ineffective their cybersecurity spending has been. But don’t blame the IT staff. Information and system availability is their job, not cybersecurity. IT administrators and managers are aware of that fact, though they’re often reluctant to admit it.
Cybersecurity professionals balance security controls and availability in the context of an organization’s business drivers and risk profile. You don’t have to sacrifice system and information availability to secure your organization. But you cannot rely solely upon IT staff. You really need a cybersecurity expert who knows the tools, techniques, and services necessary to secure your business.
As local cybersecurity experts exclusively serving small businesses, We Know Cyber fills that need. Contact us today at guy@weknowcyber.com for a free initial consultation and free vulnerability scan of your business systems and website today!